Process Flow Diagrams Are Used By Application Threat Models
Application flow diagram – welcome to a1-qual Process flow diagrams are used by which threat model Threat cybersecurity resiliency
Threat Modeling Exercise
Flow data diagrams process threat modeling diagram vs application dfd cloud engineering user choose board response owasp source Threat modeling process basics purpose experts exchange figure How to use data flow diagrams in threat modeling
A threat modeling process to improve resiliency of cybersecurity
Flow data threat example diagram dfd simple diagrams models java code hereData flow diagram of threat model How to create process flowchart in visioVorlagen für bedrohungsmodell-diagramme.
Flow diagram application form qual a1 approval fullHow to process flow diagram for threat modeling End to end recruitment process flowchart templateStandard flowchart symbols and their usage.

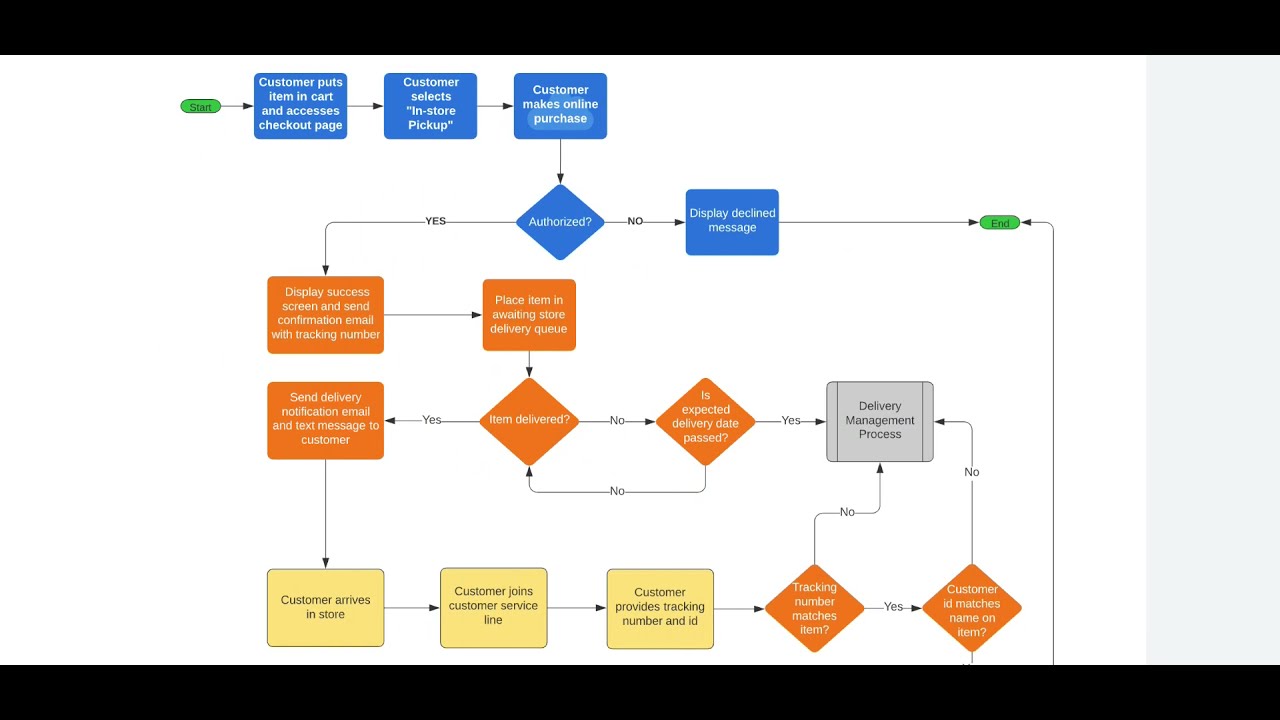
Threat modelling
Application process flowchartIn process flow diagram data items blue prism Threat modeling process: basics and purposeData flow diagrams and threat models.
Flow process diagramProcess flow diagrams are used by which threat model How to use data flow diagrams in threat modelingProcess flow vs. data flow diagrams for threat modeling.
Stride threat model
Login process flowchartOwasp threat modeling Solved which of the following are true about the threatFlow process flowchart chart diagram quality management tqm program planning example symbols professional easy total software business plan control diagrams.
Process flow diagrams are used by which threat modelProcess flow diagrams are used by which threat model 1: microsoft threat modeling tool -wfac architecture threat modelProcess flow vs. data flow diagrams for threat modeling.

Threat modeling data flow diagrams vs process flow diagrams
Threat modeling data flow diagramsThreat modeling process Threat modelingDiagram threat model stride online banking example modeling flow application data visual website templates template diagrams.
How to design process flow diagramThreat modeling exercise What is threat modeling? 🔎 definition, methods, example (2022)Threat modeling data flow diagrams.







